In many companies, the number of endpoint devices is increasing – buzzword “Internet of Things” (IoT). While networking brings many benefits to everyday business, a negative side effect is the growing attack surface for hackers that accompanies it. To reduce the attractiveness for hacker attacks, it must be continuously ensured that far-reaching security standards exist in all endpoints. An important step is therefore to extend previous security standards to growing networks.
New hacking methods require new security measures
Among other things, AI makes it possible to adapt attacks spontaneously so that they have a constantly changing characteristic and can thus cleverly circumvent existing security systems. ML comes into play in the hacker sector in the form of phishing emails, among other things. For example, security researchers at ZeroFOX were able to achieve a significantly higher success rate with phishing attacks on Twitter users using ML. They analyzed Twitter feeds using ML and then filtered out specific users for an attack. One in three users believed the phishing.
Important facets of security against cyberattacks
A common prevention measure against hacker attacks is “Zero Trust”: Ideally, users and devices should be identified and authenticated before data is shared. However, in addition to the dangers already mentioned, it may be neglected, for example, to reset the user or the device to a “zero trust state” after an access requirement has expired. Only the combination with other security measures can guarantee optimal protection of your software and cloud data.
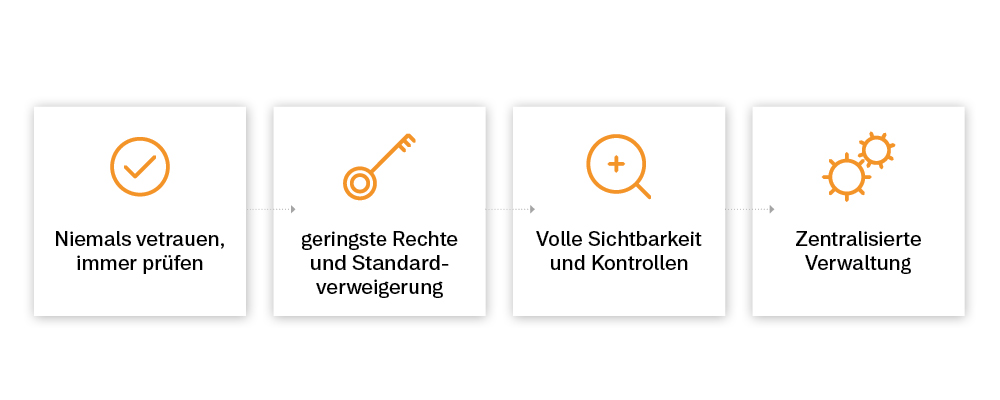
COCUS can offer your company as an external supporter a diversified expert knowledge in the IT security area for the development and expansion of a customized, effective security system.



